A rogue access point (or AP) is a wireless access point that is not managed by your network administrator because it is installed on your network without your permission. Rogue APs do not have the same security settings as other access points. These APs are physically located behind a network firewall. This means that anyone who has access to the AP has access to a wider network. A rogue AP is a wireless access point installed on a wired network infrastructure without the permission of the network administrator or owner to provide rogue wireless access to the network's wired infrastructure. There is likely to be. Anyway, rogue access points can be used in a variety of attacks, including denial of service, data theft, and other malware implementations.
In this post we are going to use WifiPumpkin tool. Wifipumpkin3 is a powerful framework for rogue access point attacks which is written in Python that allows security researchers, red teams, and reverse engineers to set up wireless networks to carry out man-in-the-middle attacks.
Features -
- Creates rogue access point attack
- Good for Man-in-the-middle attacks
- Plenty module for deauthentication attacks
- Provides Rogue Dns Server
- Can intercept, inspect, modify and replay web traffic
- Provides DNS monitoring service
- Can harvest credentials
Installation
1) Update packages
$ sudo apt-get update
2) Install required packages
$ sudo apt-get install hostapd python3.9-dev libssl-dev libffi-dev build-essential python3.9 python3-pyqt5
3) Install wifipumpkin3
$ git clone https://github.com/P0cL4bs/wifipumpkin3.git $ cd wifipumpkin3 $ sudo python3 setup.py install
4) Now just run this tool by typing -
$ sudo wifipumpkin3
If you have any problems regrading this, please comment below.
Also Read -
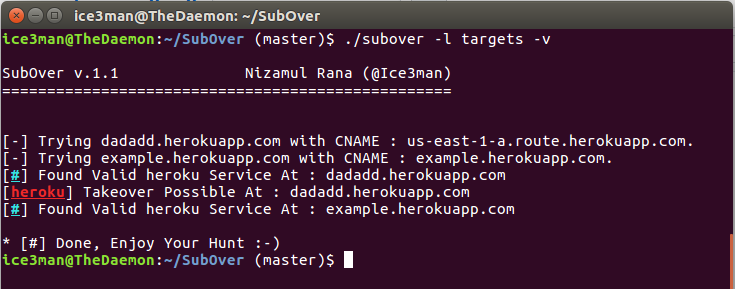
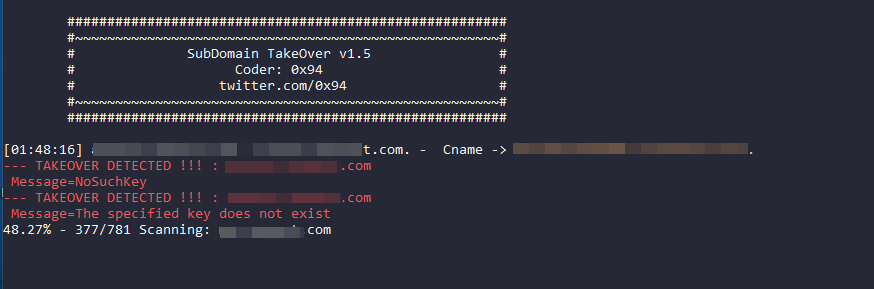
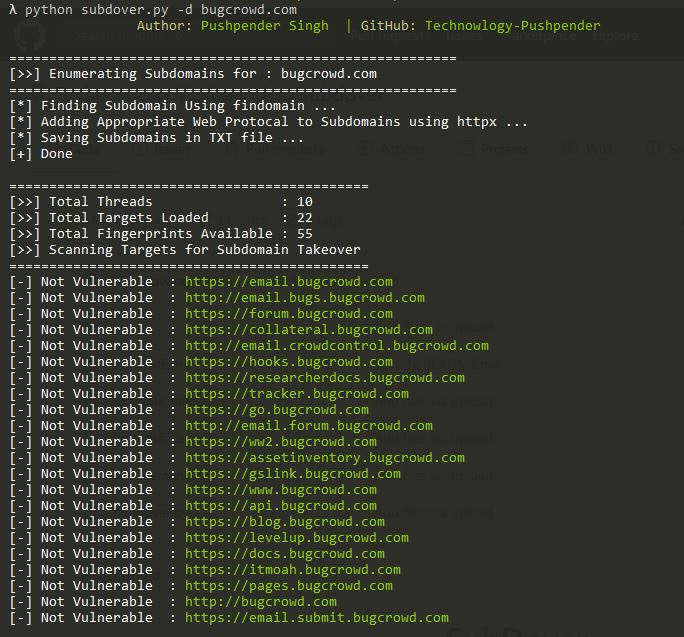
Top 5 Subdomain Takeover Tools for Linux [2021]
How to install kali linux repo in any debian based distro

.webp)