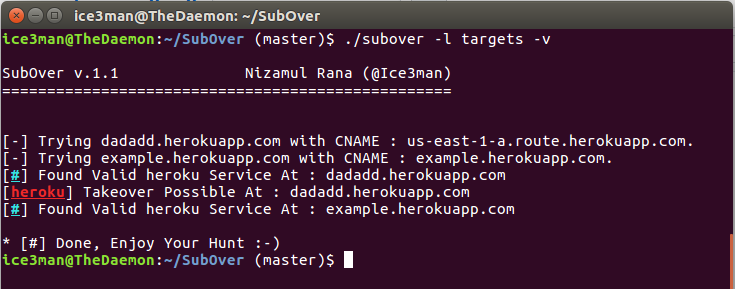
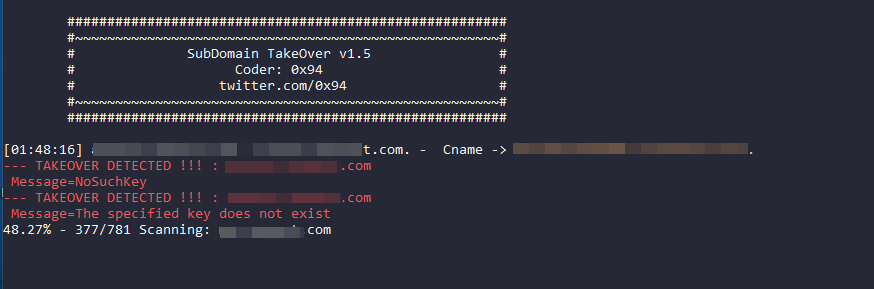
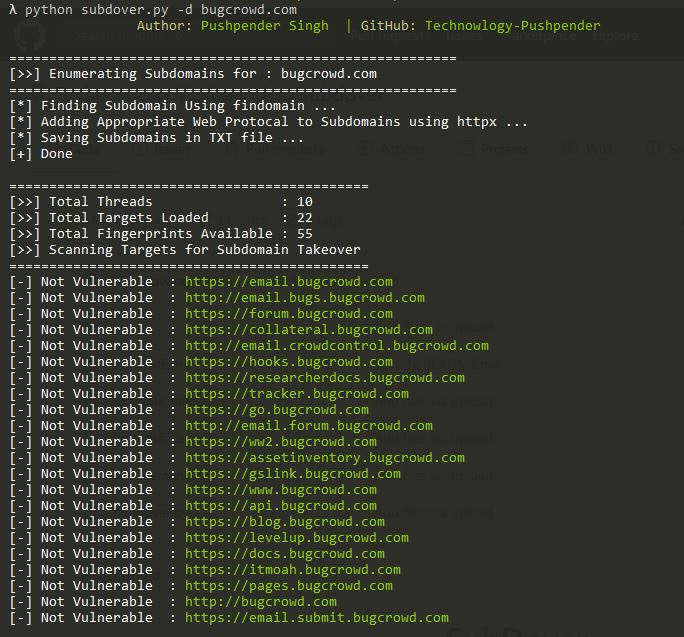
Microsoft has warned of a new Windows zero-day exploit that is being actively exploited by attackers. The exploit affects all supported versions of Windows, including Windows 10 and Windows 11.
The exploit is a remote code execution vulnerability that allows attackers to execute arbitrary code on a victim's computer. This could allow attackers to steal data, install malware, or take control of the victim's computer.
The vulnerability is tracked as CVE-2023-29336 and is a heap buffer overflow in the Win32k kernel driver. The vulnerability can be exploited by sending a specially crafted packet to a vulnerable system.
Microsoft has released a security update to address the exploit. The update is available for Windows 10 and Windows 11. It is important to install the update as soon as possible to protect yourself from the exploit.
Here are some tips for staying safe:
- Keep your software up to date. Microsoft releases security updates regularly to address vulnerabilities such as this one. It is important to install these updates as soon as they are available.
- Use a security solution. A security solution can help to protect your computer from malware and other threats.
- Be careful about what you click on. Do not click on links in emails or on websites that you do not trust.
- Use strong passwords. Use strong passwords and change them regularly.
- Back up your data regularly. In the event that your computer is infected with malware, you will be able to restore your data from a backup.
By following these tips, you can help to protect yourself from the new Windows zero-day exploit.
If you think that you have been infected with malware, there are a few things that you can do:
- Run a virus scan. A virus scan can help to identify and remove malware from your computer.
- Change your passwords. Change your passwords for all of your online accounts.
- Monitor your credit report. Monitor your credit report for any unauthorized activity.
By taking these steps, you can help to minimize the damage caused by a malware infection.












.webp)